DNS cache poisoning, also known as DNS spoofing, is a type of attack that exploits vulnerabilities in the domain name system (DNS) to divert Internet traffic away from legitimate servers and towards fake ones.
One of the reasons DNS poisoning is so dangerous is because it can spread from DNS server to DNS server. In 2010, a DNS poisoning event resulted in the Great Firewall of China temporarily escaping China’s national borders, censoring the Internet in the USA until the problem was fixed.
How DNS Works
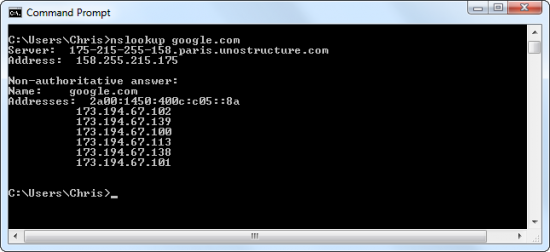
Whenever your computer contacts a domain name like “google.com”, it must first contact its DNS server. The DNS server responds with one or more IP addresses where your computer can reach google.com. Your computer then connects directly to that numerical IP address. DNS converts human-readable addresses like “google.com” to computer-readable IP addresses like “173.194.67.102”.
DNS Caching
The Internet doesn’t just have a single DNS server, as that would be extremely inefficient. Your Internet service provider runs its own DNS servers, which cache information from other DNS servers. Your home router functions as a DNS server, which caches information from your ISP’s DNS servers. Your computer has a local DNS cache, so it can quickly refer to DNS lookups it’s already performed rather than performing a DNS lookup over and over again.
DNS Cache Poisoning
A DNS cache can become poisoned if it contains an incorrect entry. For example, if an attacker gets control of a DNS server and changes some of the information on it — for example, they could say that google.com actually points to an IP address the attacker owns — that DNS server would tell its users to look for Google.com at the wrong address. The attacker’s address could contain some sort of malicious phishing website.
DNS poisoning like this can also spread. For example, if various Internet service providers are getting their DNS information from the compromised server, the poisoned DNS entry will spread to the Internet service providers and be cached there. It will then spread to home routers and the DNS caches on computers as they look up the DNS entry, receive the incorrect response, and store it.
Whereas unauthenticated responses target a requester, DNS cache poisoning targets any type of caching DNS server. An attacker observes a DNS request and generates a forged DNS reply. The reply appears authoritative and contains a long cache timeout value.
A poisoned DNS server will provide the false data to any data request. For example, a caching DNS server can be poisoned so that the hostname www.happydomain.lan is mapped to the localhost address (127.0.0.1). Any DNS host requesting a lookup for www.happydomain.lan receives the localhost address rather than the true address. This makes the domain unreachable. Moreover, the incorrect information will be provides as long as the poisoned information is in the cache.
There are few viable options for mitigating DNS cache poisoning. DNS servers may be configured with an upper limit for cached data storage. For example, if the server is configured for a maximum cache period of 24 hours, then a poisoned reply containing a 7-day cache timeout will expire after 24 hours. However, the attack is still viable for the 24-hour window.
Although an attacker can generate a fake DNS reply, they cannot easily prevent a valid DNS server from replying. Caching servers may discard cache entries when multiple replies are received with differing values. This prevents the propagation of tainted information (but impacts the cache performance).
Blind ID Attack
Unauthenticated responses and cache poisoning usually require an attacker to observe the DNS request and session identifier. But observing a request is not always essential. An attacker may choose a common domain name and begin an attack when the hostname appears to timeout. This attack method generates a flood of DNS replies, each containing a different session identifier.
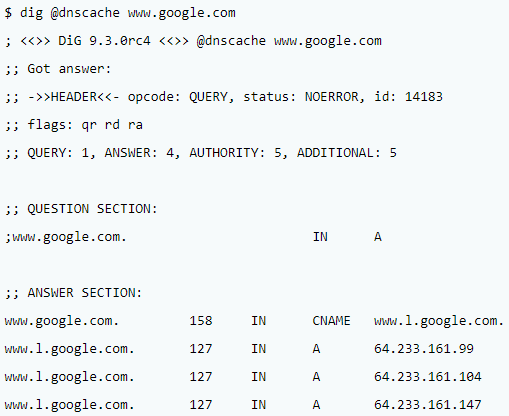
For example, consider a caching server with data that expires in a few seconds. In this example, the hostname entry expires in 158 seconds, and the IP addresses expire in 127 seconds. When they expire, the caching server (dnscache) relays the next request to other DNS servers. The replies from these servers repopulate the cache.
Because the attacker knows when the cache expires, the attack can be precisely timed. The only thing needed is for the caching server to generate a request after the cache expires. The attacker can initiate this process by sending a request to the server when the cache is known to expire.
During this window of opportunity, the attacker can generate 65,536 false DNS packets-one for each session identifier. If the correct session identifier is generated before a real server can provide the true reply, then the caching server becomes poisoned. If the attack fails, then the attacker must wait for the cache to expire before trying again. This type of attack is a race condition; the attack does not always succeed. If tried enough times, however, it will eventually succeed.
Example Listing of a DNS Cache Expiration
In theory, a blind attacker must also guess the UDP port number, however, most DNS servers reuse the same port number for subsequent queries. By reusing the same port, the DNS software does not need to manage a suite of UDP network connections and does not spend time binding to new UDP ports. Unfortunately, this also means that the attacker can determine the port to attack before initiating the attack. Although rare, DNS servers can rotate their UDP ports when making queries. This lessens the risk from a blind attack but increases the software complexity because multiple ports must be managed.
DNS Spoofing vs. DNS Cache Poisoning
Often interpreted as the same type of attack, in reality these two techniques are technically different from one another. Generally speaking, we could say that DNS Cache Poisoning is one of the many ways to achieve DNS Spoofing, which refers to the wide range of existing attacks aimed at supplanting the information stored on DNS servers.
DNS Spoofing would represent the ultimate goal of the attack (to manage to change the registries stored on the DNS server in whatever way the attackers decide), for which different mechanisms are used. They include DNS Cache Poisoning, but also man-in-the-middle attacks, the use of fake base stations, and even compromising the security of the DNS server.
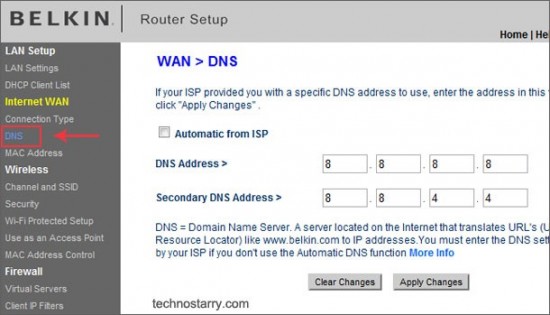
We can also see examples of DNS spoofing in attacks aimed at users. One of these would be supplanting the address of the DNS servers configured on our operating system or router. The usual way is to enter the address of the DNS servers of our internet service provider, or those of another organization such as Google, as we can see below:
DNS Cache Poisoning refers to the situation in which many end users use the same cache, where the registries that are stored correlate each IP address with a domain. In the event attackers manage to manipulate a DNS entry in this registry, the internet service providers that use this cache would accept it as authentic, even if it has been manipulated to point to a fake website.
What about DNS hijacking?
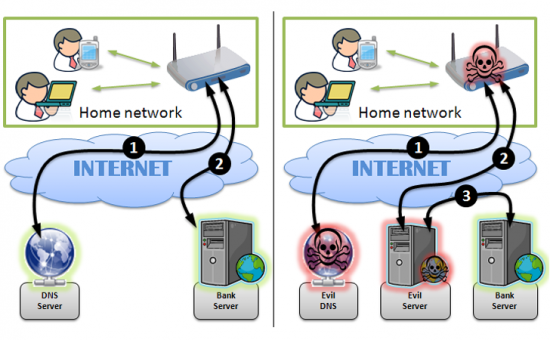
Malware can also be used to affect the resolution of domain names so the victims connect to a server controlled by the criminals. There are examples of malware like Win32/DNSChanger, which modify the DNS established by the user or our internet service provider. We can see how they work in the following image:
This enables the attackers to carry out a wide variety of attacks, ranging from phishing – in other words using fake websites which the victim visits thinking they are real (having accessed them by entering the correct address in their browser) – to the use of exploits to take advantage of vulnerabilities while the user is browsing what are believed to be trusted web pages but which have in fact been generated by the attackers in order to infect the user.
The clearest example, however, is that of networks of zombie computers, otherwise known as botnets. A lot of these modify the DNS servers that their victims have configured, making them point to others controlled by the attackers. This way, as well as the malicious actions we have already described, the criminals can send commands to the bots, update the version of the malware, or even remove it from the system if necessary.