To totally unlock this section you need to Log-in
Login
Organizations using Active Directory for their DNS service should take advantage of Windows PowerShell to manage bulk permission changes. This how-to will walk you through finding DNS object ACLs and adding DNS object ACEs.
Active Directory (AD) is an enormously popular directory service from Microsoft. AD provides a plethora of services, including single sign-on (SSO) authentication, group policy configuration management, printer management, and more. One of the requirements of AD is Domain Name System (DNS). AD heavily depends on DNS for many of its core features. Due to this requirement, many organizations also choose AD as their primary DNS service for clients and servers. IT organizations point systems to AD domain controllers for internal (and external) name resolution, which leads to a critical reliance on AD DNS.
When an organization uses AD for their DNS service, their DNS zones are AD-integrated. When this happens, DNS records get moved from being stored in a simple text file to actual Active Directory objects inside of the AD database. This comes with several benefits, such as being able to leverage AD’s robust replication technologies and provide DNS services to geographically dispersed locations, automatic DNS record creation for systems, and much more.
However, this reliance on AD also comes with AD's object security model, which can sometimes get confusing. Large enterprises can potentially have tens or hundreds of thousands of DNS records, which, if AD-integrated, are all AD objects. If bulk permission changes must be made across these objects, it's important to know how to properly manage them with Windows PowerShell.
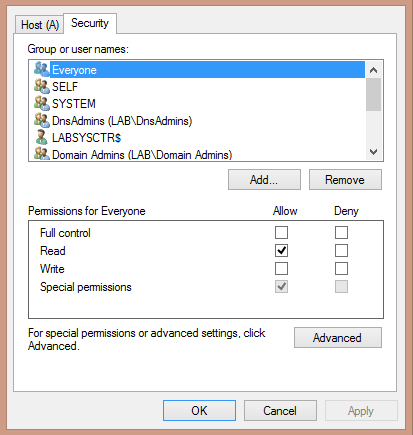
Each DNS record, or AD object, has a familiar Security tab when viewing the Properties.
DNS objects follow the same security model as many other common objects in the Microsoft environment including files, folders, registry keys/values, and so on. Each DNS object has an assigned Access Control List (ACL) with numerous Access Control Entries (ACEs) inside it. The ACE is made up of a security identity (a username or group) and a set of various permissions indicating what that security identity can do to that object.
To change these permissions, you can simply open up the DNS management tool, right-click on a DNS record, go to Properties, click the Security tab, and you’re off to the races. But what if you need to retrieve or modify existing permissions, or you need to create new ACEs altogether on many DNS objects at once? The answer is to use PowerShell.
Understanding DNS Objects In AD
Before using PowerShell, you must first understand how AD stores DNS records. When integrating DNS into AD, the DNS objects (or dnsNode objects) are always stored in AD’s root or the RootDSE.
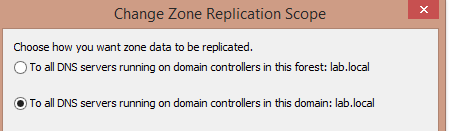
From there, whether the admin chooses domain-wide or forest-wide replication depends on where the dnsNode objects reside.
dnsNode objects are stored forest-wide in dnsZone containers located in the path:
DC=domain.com,CN=MicrosoftDNS,DC=ForestDnsZones,DC=domain,DC=com.
If they’re stored domain-wide, they would be located at:
DC=domain.com,CN=MicrosoftDNS,DC=DomainDnsZones,DC=domain,DC=com.
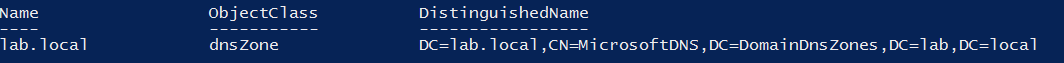
To find all dnsZone containers, you may use the PowerShell command Get-Item and utilize the Active Directory module’s AD drive.
$DomainName = ‘domain.com’ $AdIntegrationType = ‘Domain’ $DomainDn = (Get-AdDomain).DistinguishedName Get-Item "AD:DC=$DomainName,CN=MicrosoftDNS,DC=$AdIntegrationType`DnsZones,$DomainDn"
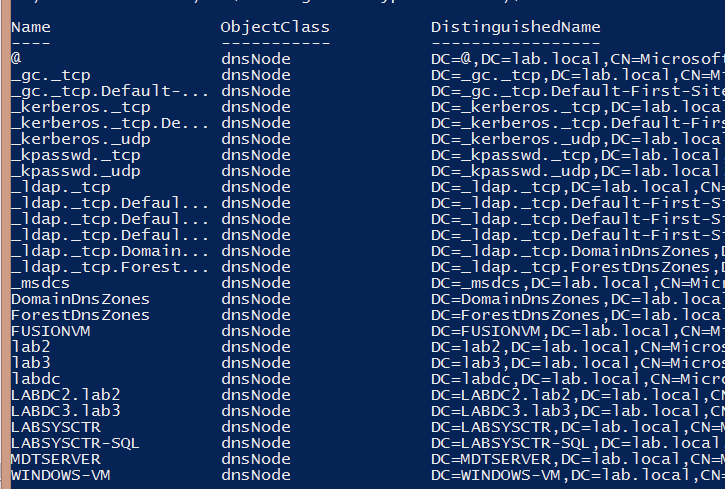
Once you’ve found the dnsZone containers, you can now enumerate dnsNode objects, which represent the records themselves.
$DomainName = ‘domain.com’ $AdIntegrationType = ‘Domain’ $DomainDn = (Get-AdDomain).DistinguishedName Get-ChildItem "AD:DC=$DomainName,CN=MicrosoftDNS,DC=$AdIntegrationType`DnsZones,$DomainDn"
Finding DNS Object ACLs
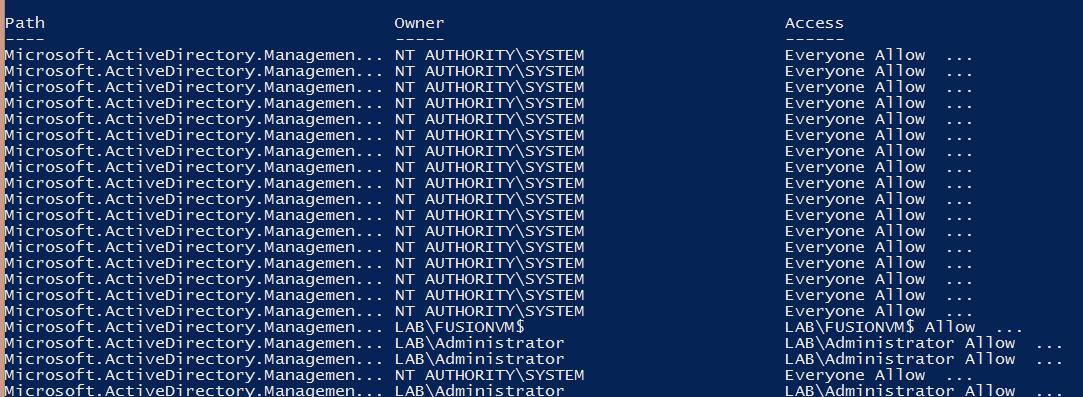
By this point, you can simply include PowerShell’s Get-Acl cmdlet to grab the ACLs for each of the objects.
$DomainName = ‘domain.com’
$AdIntegrationType = ‘Domain’
$DomainDn = (Get-AdDomain).DistinguishedName
Get-ChildItem "AD:DC=$DomainName,CN=MicrosoftDNS,DC=$AdIntegrationType`DnsZones,$DomainDn" | foreach {
Get-Acl -Path “ActiveDirectory:://RootDSE/$($_.DistinguishedName)”
}
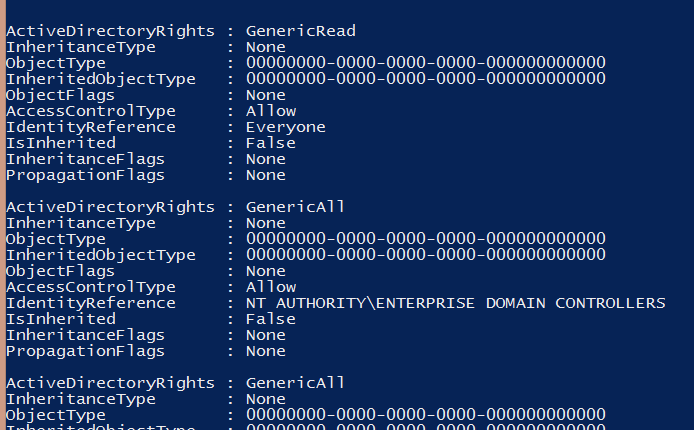
Expand the Access property on the ACL object to dig in a little deeper.
(Get-Acl -Path “ActiveDirectory:://RootDSE/$($_.DistinguishedName)”).Access
Adding DNS Object ACEs
You should now be able to find ACLs on your DNS objects. Now that you know where the objects are and how to retrieve them, it's possible to append additional ACEs to the objects.
Adding ACEs to ACLs attached to AD objects requires three properties:
- Security Identifier (SID)
- Rights (Full Control, Modify, Read, and so on)
- Type (Allow or Deny)
The first thing you must do is retrieve the SID of the security identity you’ll be adding to this ACE. A security identity is something like an AD user account, computer account, or group. To do this, you’ll use the Get-AdUser cmdlet. One of the properties of the result of this cmdlet is the property ObjectSID.
Let’s say we'd like to add permission for a user account called abertram. To find the SID of abertram, we can use Get-AdUser in this manner.
$Sid = (Get-ADUser abertram -Properties ObjectSID).ObjectSID.Value
Next, you’ll need to create an object using three parameters: the SID, rights, and the type of permission:
System.DirectoryServices.ActiveDirectoryAccessRule
In this instance, we want to give the user account Modify rights to this object:
$AccessRule = New-Object System.DirectoryServices.ActiveDirectoryAccessRule($Sid, ‘Modify’, ‘Allow’)
Once we build this object, we can then add it to the existing ACL object we built earlier using Get-ChildItem.
$Acl.AddAccessRule($AccessRule)
Finally, after our ACL object is built, all that’s left to do is apply the ACE to the object, and we’re done.
Set-Acl -Path "ActiveDirectory:://RootDSE/$($AdObject.DistinguishedName)" -AclObject $Acl
To add this ACE to all records, we build upon our previous code and eventually come to a script that looks like this.
$DomainName = ‘domain.com’
$AdIntegrationType = ‘Domain’
$DomainDn = (Get-AdDomain).DistinguishedName
$Sid = (Get-ADUser abertram -Properties ObjectSID).ObjectSID.Value
$AccessRule = New-Object System.DirectoryServices.ActiveDirectoryAccessRule($Sid, ‘Modify’, ‘Allow’)
Get-ChildItem "AD:DC=$DomainName,CN=MicrosoftDNS,DC=$AdIntegrationType`DnsZones,$DomainDn" | foreach {
$Acl = Get-Acl -Path "ActiveDirectory:://RootDSE/$($_.DistinguishedName)"
$Acl.AddAccessRule($AccessRule)
Set-Acl -Path "ActiveDirectory:://RootDSE/$($_.DistinguishedName)" -AclObject $Acl
}
Working with Active Directory object permissions is a little complicated. To truly understand this concept, it’s helpful to know a little about the structure of AD and how objects are organized. Also, once you’re able to understand that DNS records are represented by dnsNode objects in Active Directory and how to access them, the task becomes easier.