To totally unlock this section you need to Log-in
Login
When connecting to a VMWare vCenter server using a web-browser, there appears a warning of self-signed certificate issued by an untrusted certification authority. In Firefox, this warning can be disabled just by adding a vCenter website to the list of exceptions, but in Internet Explorer the procedure is more complicated.
SSL certificates installed by default with ESXi and vCenter servers are self-signed, so other systems do not trust them and show a warning or block the connection with these websites. To disable the warning of a self-signed certificate, you can add the self-signed certificate it the list of trusted certificates or replace the certificate with your own one issued by a trusted certification authority. We’ll consider the first variant, the procedure is trivial, but there are some not quite obvious moments.
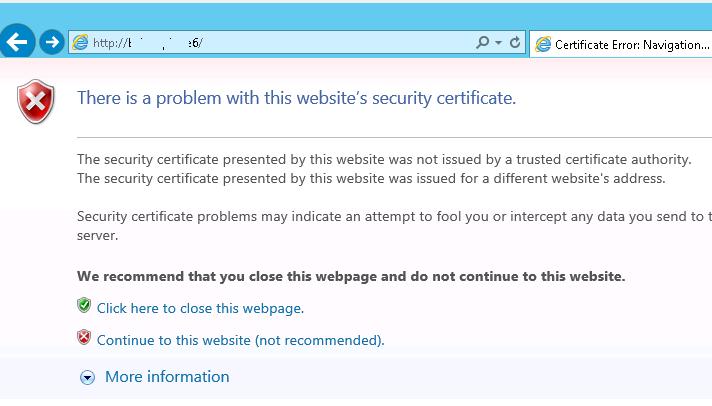
So when opening a vCenter server webpage, by going to https://vCenter-IP-address/ in your web browser, a window with the following warning appears:
There is a problem with this website’s security certificate. The security certificate presented by this website was not issued by a trusted certificate authority. The security certificate presented by this website was issued for a different website’s address. Security certificate problems may indicate an attempt to fool you or intercept any data you send to the server.
NOTE: The warning The security certificate presented by this website was issued for a different website’s address is shown since in our case the host name is different from the CN name, for which the certificate is issued. In order this warning is not shown, in the browser you have to open the FQDN server name, for which the certificate is issued. By the way, to make it more convenient you can replace this certificate for your own one created using New-SelfSignedCertificate cmdlet, which allows to issue a certificate for any set of CN.
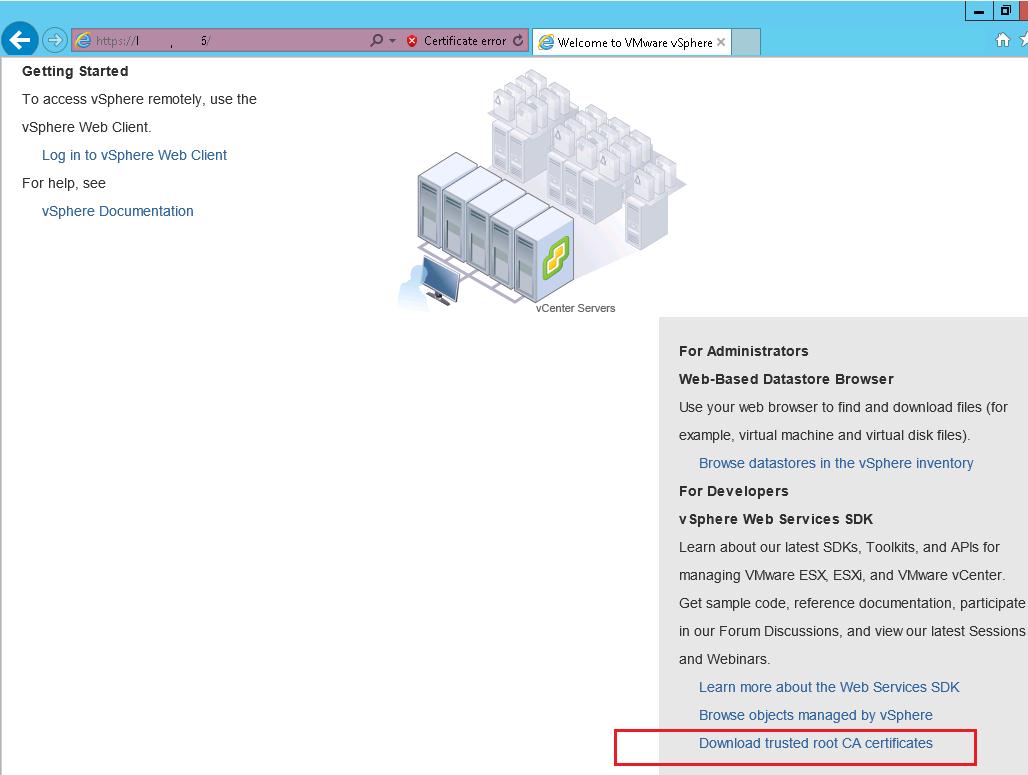
Having clicked Continue to this website link (not recommended), you can go to vCenter Getting Started page. To download the certificate, click Download trusted root CA certificates.
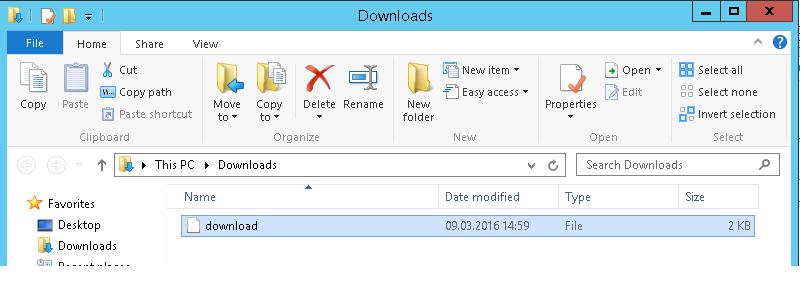
Save the file to any directory. The name of the file is download (with no extension).
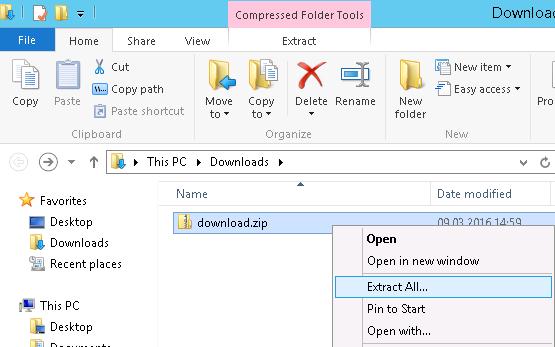
Then change the extension of download to download.zip and extract it with the built-in archiver (Extract All) or with any other third-party archiver, like WinZip, WinRAR or 7zip.
The cert archive contains 2 files with the extensions .0 and .r0. Change the file extension .0 to .cer.
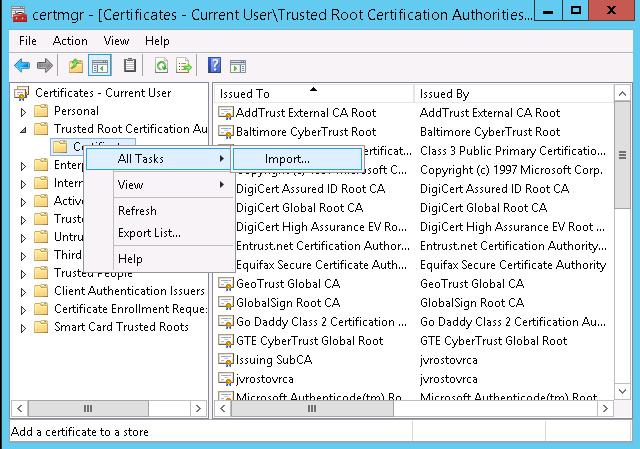
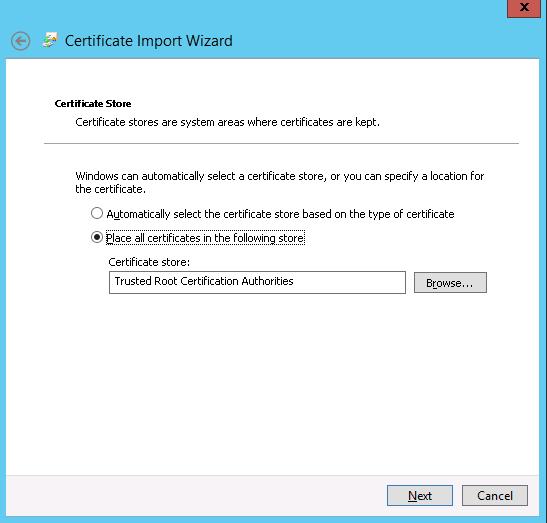
Now you only have to add this root CA certificate to the list of trusted certificates. Suppose, we want this certificate to be trusted only with the current account. Open certmgr.msc console, go to Certificates > Trusted Root Certification Authorities and open the certificate import wizard (Import) in the context menu.
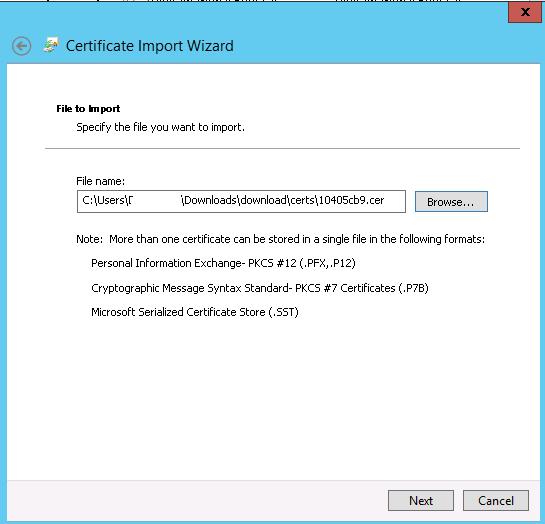
Select the certificate file obtained earlier and place it to the Trusted Root Certification Authorities store.
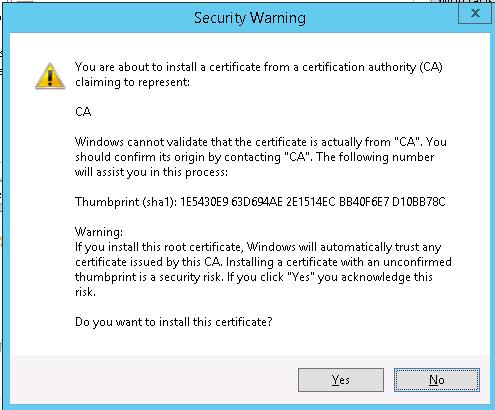
Submit adding the certificate.
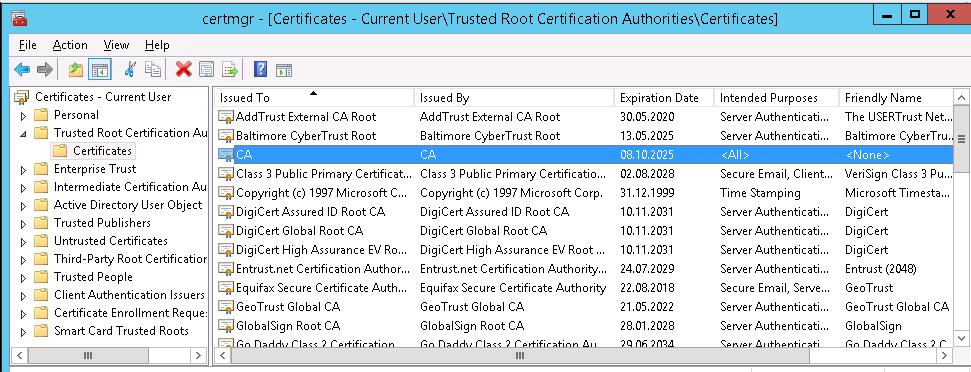
A new certificate with the name CA appears in the list.
Open the vCenter webpage in the browser again. The warning won’t appear.
These guidelines are applicable to vCenter Server Appliance, if you are using Windows vCenter Server, you won’t be able to download the certificate file, since there will be no link to download the archive with the certificate. This file is stored on vCenter Server (running Windows) in C:\ProgramData\VMware\SSL\. (C:\Program Data\VMware\VMware VirtualCenter\SSL in earlier versions.) The certificate from this directory has to be imported on a client in the same way.
Active Directory Group Policy Update in Deployments with VMCA as an Intermediate Certificate Authority
This procedure is for you if your environment has these characteristics:
You can import the root certificate into the group policy of your Active Directory environment to make the certificates trusted in your Active Directory domain. After the certificates are trusted, the browser error no longer appears on any machine that is part of the Active Directory domain.
From a client system Web browser, go to the base URL of the vCenter Server system or the vCenter Server Virtual Appliance without appending port numbers or vsphere-client extension.
https://vcenter.domain.com/
- Click the Download trusted root CA certificates link at the bottom of the grey box on the right and download the file.
- Change the extension of the file to .zip.
- The file is a ZIP file of all root certificates and all CRLs in the VMware Endpoint Certificate Store (VECS).
- Extract the ZIP file.
The result is a .certs folder that contains two types of files. Files with a number extension (.0, .1, and so on) are root certificates. Change the extension to .crt. Files with a extension that starts with an r (.r0,. r1, and so on) are CRL files associated with a certificate. Change the extension to .crl.
- Open the Active Directory Group Policy Management Editor.
- Open Public Key Policies and select Trusted Root Certificate Authorities.
- Add the certificate file or files that you downloaded.
- From you Windows command prompt, run gpupdate /force to force an update.
Firefox has its own trusted roots store and does not use the operating system store. If you are working with Firefox, download the certificate as described above, and then select Tools > Options, click Advanced, and click Certificates to import the certificate into Firefox.